Network Segmentation: Reducing Your PCI DSS Environment Scope
Understanding network segmentation for PCI DSS compliance
Payment card industry data security standard (PCI DSS) compliance remain one of the well-nigh significant regulatory challenges for businesses that handle credit card information. Among the various strategies to manage this compliance burden, network segmentation stand out as especially effective. But what precisely is network segmentation, and how can it help your business reduce the scope of your PCI DSS environment?
What’s network segmentation?
Network segmentation is the practice of divide a computer network into smaller, isolate sections or segments. Each segment functions as a separate network with specific security controls, access restrictions, and monitor capabilities. Think of it as create separate rooms in a building, each with its own lock and key, kinda than have one open space where everyone have access to everything.
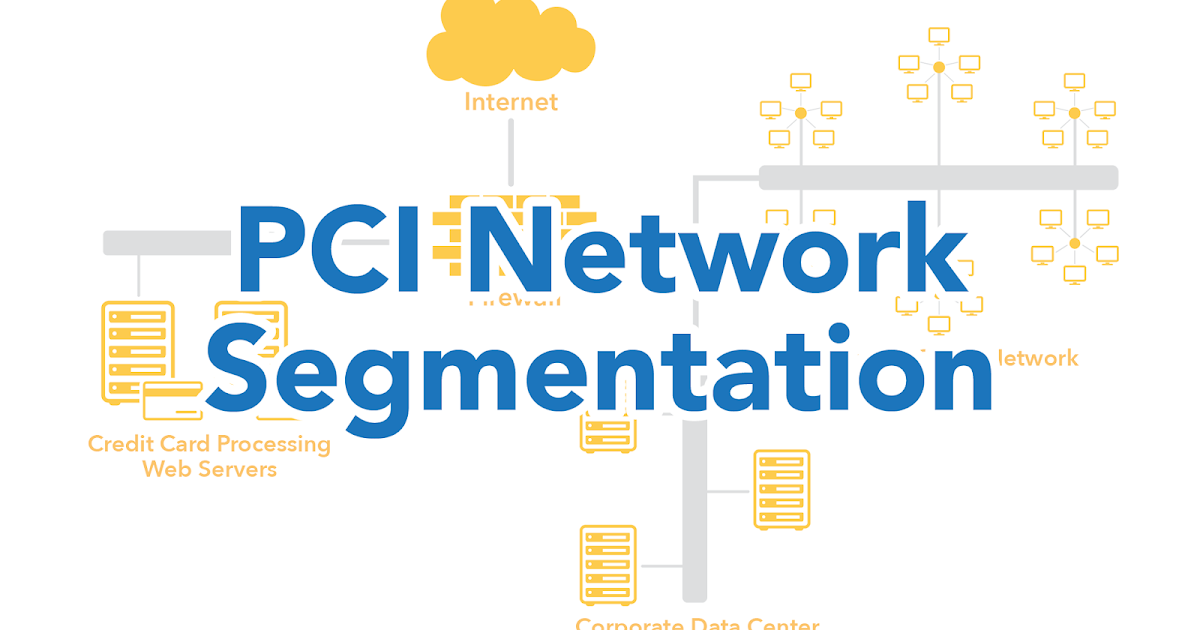
In the context of PCI DSS, network segmentation create boundaries between systems that store, process, or transmit cardholder data (the cCDEor cardholder data environment )and those that don’t. This separation is not simply logical but must bebe enforcedhrough technical controls.
The relationship between network segmentation and PCI DSS scope
The scope of PCI DSS refer to all the systems, people, processes, and technologies that are involved in store, processing, or transmit cardholder data. Without proper segmentation, your entire network might fall within this scope, require all systems to comply with the full set ofPCIiDSSs requirements.
Nonetheless, with effective network segmentation, you can isolate the systems that handle cardholder data from the rest of your network. This mean that solely the segment portions need to meet the stringent PCI DSS requirements, potentially reduce your compliance burden importantly.
Benefits of use network segmentation for PCI DSS
Reduced compliance scope
The virtually immediate benefit of network segmentation is scope reduction. By isolate cardholder data environments, you limit the number of systems subject to PCI DSS requirements. This translates direct into:
- Fewer systems to secure and monitor
- Reduced documentation requirements
- Simplify compliance audits
- Lower overall compliance costs
For many businesses, this scope reduction can mean the difference between an overwhelming compliance project and a manageable one.
Enhanced security posture
Beyond compliance benefits, network segmentation importantly improve your overall security stance:
- Containment of breaches: if one segment is compromise, the breach is contained and can not well spread to other parts of the network
- Defense in depth: create multiple layers of security that an attacker must penetrate
- Reduced attack surface: limits the points of entry for potential attackers
- Granular access control: allow precise management of who can access sensitive data
Operational efficiency
Wellspring design segmentation can besides improve network performance and management:
- Better network traffic management
- Improved troubleshooting capabilities
- More effective resource allocation
- Simplify network changes and updates
Implement effective network segmentation
Identify your cardholder data environment
The first step in implements network segmentation forPCIiDSSs is to identify precisely where cardholder data exist in your environment. Thisrequirese:
- Data flow mapping to track how cardholder data move through your systems
- Inventory of all systems that store, process, or transmit cardholder data
- Identification of connected systems that could provide access to cardholder data
Many organizations discover during this process that cardholder data exist in places they weren’t aware of, such as backup systems, test environments, or log files.
Technical implementation approaches
Several technologies can be used to implement network segmentation:
Firewalls and access control lists (aACLs)
Firewalls remain the primary tool for network segmentation. Next generation firewalls can provide deep packet inspection and application level filtering, ensure that just authorized traffic crosses segment boundaries. ACLs on routers and switch complement firewalls by provide additional traffic filtering.
Virtual local area networks (vplans)
Plans allow you to create logical network segments within a physical network infrastructure. While plans entirely are not sufficient for PCI DSS segmentation, they form an important component when combine with firewalls and other security controls.
Physical network separation
In some cases, complete physical separation of networks may be appropriate, especially for the virtually sensitive cardholder data environments. This approach provide the strongest segmentation but can be costly and less flexible.
Zero trust architecture
The zero trust model assume that threats exist both within and outside the network, require verification for anyone try to access resources, disregardless of their location. This approach is progressively relevant for PCI DSS environments, peculiarly with remote work become more common.
Common segmentation architectures
Flat network with cardholder data segment
The simplest approach is to create a separate, secured segment for all systems handle cardholder data, with strict controls on connections between this segment and the rest of the network.
Multi tier segmentation
More sophisticated implementations might include multiple tiers:

Source: hunterfiber.com
- Outer tier: general business systems with no cardholder data
- Middle tier: systems that connect to the cardholder environment but don’t store data
- Inner tier: core cardholder data environment with the strictest controls
Micro segmentation
Advanced approaches may implement micro segmentation, where security controls are applied at the individual workload level. Thiprovidesde the virtually granular control but require sophisticated management tools.
Common challenges and solutions
Technical challenges
Implement effective segmentation frequently face technical hurdles:
Legacy systems
Older systems may not support modern segmentation technologies. Solutions include:
- Use compensate controls
- Implement gateway systems that mediate access
- Plan for system replacement when feasible
Complex applications
Many business applications have complex communication requirements that make segmentation challenge. Address this by:
- Detailed application dependency mapping
- Work with vendors to understand communication requirements
- Implement application aware security controls
Organizational challenges
Resistance to change
Users and business units may resist segmentation due to perceive impacts on functionality or convenience. Overcome this by:

Source: blog.securitymetrics.com
- Clear communication about security benefits
- Phased implementation to minimize disruption
- Executive sponsorship to reinforce importance
Skills gap
Implement and maintain segmentation require specialized skills. Address this done:
- Staff training and certification
- Engage external expertise when need
- Implement automation to reduce complexity
Validate your segmentation effectiveness
Penetration testing
PCI DSS require penetration testing to verify segmentation effectiveness. This involves attempt to breach segmentation controls from both within and outside the cardholder data environment to ensure they work as intend.
Continuous monitoring
Segmentation is not a one time project but require ongoing monitoring:
- Network traffic analysis to detect unauthorized communication attempts
- Configuration management to prevent drift from secure baselines
- Alert mechanisms for potential segmentation failures
Regular reassessment
As your business and technology environment evolve, segmentation must be reassessed:
- Annual formal reviews of segmentation architecture
- Evaluation of segmentation impact before major system changes
- Update documentation to reflect current state
Case studies: successful segmentation implementations
Retail business transformation
A mid-sized retailer with 200 locations was struggle with PCI DSS compliance across their entire network. By implement network segmentation, they isolate point of sale systems and payment processing servers from other business systems. This reduces theirPCIiDSSs scope by roughly 70 %, importantly reduce compliance costs and improve their security posture.
Healthcare provider with payment processing
A healthcare organization that handle both protect health information (phi )and payment card data face dual compliance requirements with hiHIPAAnd pcPCIsDSSThrough careful segmentation, they create separate environments for patient data and payment processing, with control interfaces between them. This not merely simplified compliance but toto improveheir ability to demonstrate regulatory adherence to auditors.
Future trends in network segmentation for PCI DSS
Cloud native segmentation
As more businesses move cardholder data environments to the cloud, segmentation approaches are evolved. Cloud native segmentation use technologies like security groups, virtual private clouds, and software define networking to create isolation without traditional network hardware.
Segmentation automation
Automated tools are emerged that can discover data flows, recommend segmentation strategies, and eventide implement and maintain segmentation policies. These tools reduce the operational burden of maintain effective segmentation.
Integration with zero trust
The zero trust security model is progressively being integrated with network segmentation strategies. This approach emphasize verification of every access attempt disregarding of source, complement traditional segmentation boundaries.
Conclusion: is network segmentation right for your business?
Network segmentation offer significant benefits for businesses seek to manage PCI DSS compliance expeditiously. By reduce scope, enhance security, and improve operational efficiency, segmentation can transform your approach to protect cardholder data.
Yet, effective implementation require careful planning, appropriate technology choices, and ongoing management. The investment in segmentation should be weighed against the potential benefits in reduce compliance costs, improve security, and lower breach risk.
For most businesses that handle payment card data, some form of network segmentation is not equitable beneficial but progressively essential. The question is not whether to segment, but how to implement segmentation virtually efficaciously for your specific environment.
By understand the principles outline in this article and apply them to your unique business context, you can develop a segmentation strategy that importantly reduce your PCI DSS compliance burden while strengthen your overall security posture.